Sometimes you might have a complex iptables setup that makes it difficult to follow packets around as they traverse the tables and chains. Using the watch utililty can help debug packet routing by visually showing highlighting rules as they are triggered.
Lets say you have configured iptables on a Linux host to drop certain packets - so you’ve put some rules into the INPUT chain in the filter table.
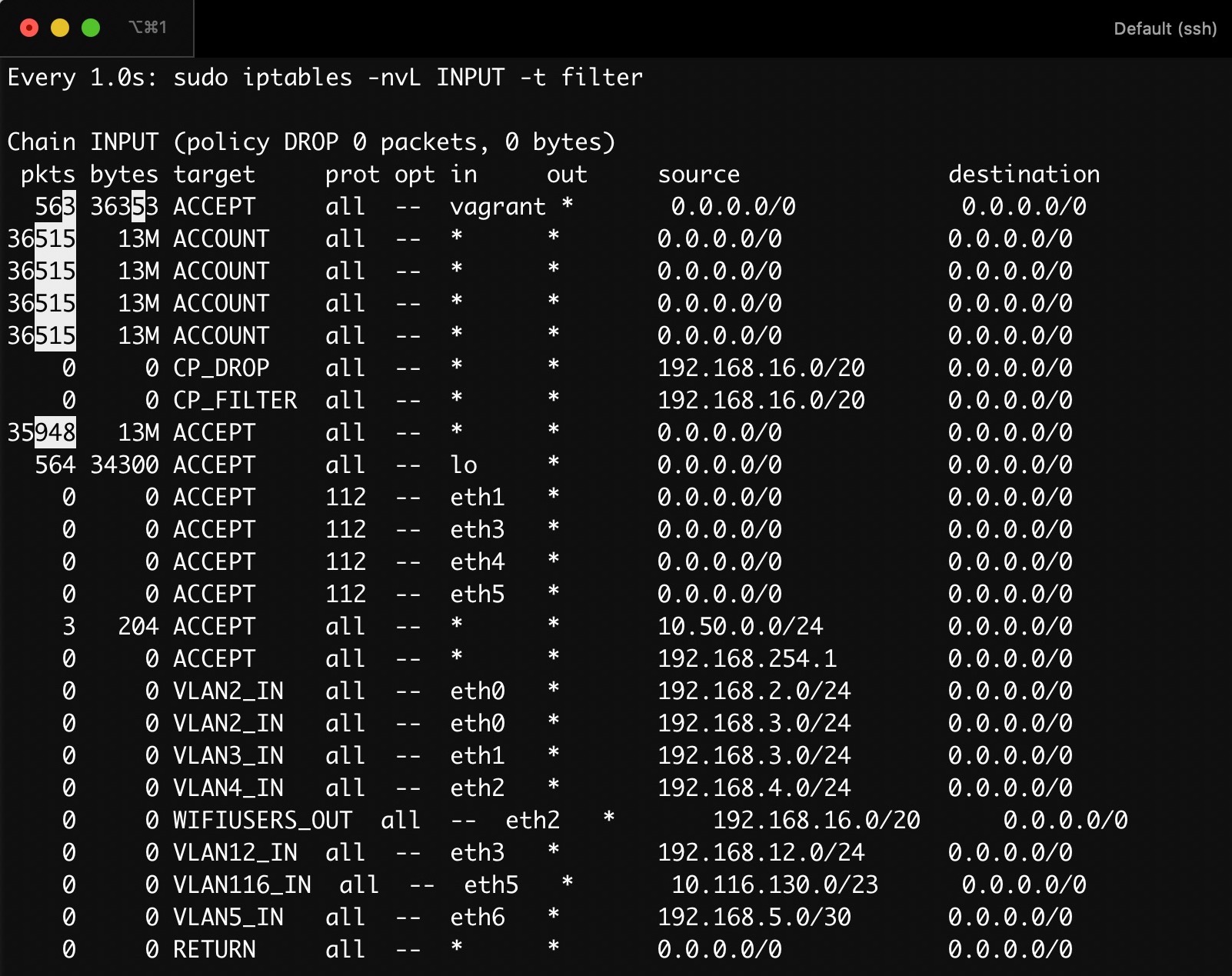
If you want to see packet counters incrementing in (near) real time, you can use the watch command on iptables. I’m using iptables with my preferring options: -nv. -v for the packet and byte counters, and -n to avoid possibly lengthy hostname lookups. The -L option is to list all rules in the given chain.
$ watch -d -n 1 'sudo iptables -nvL INPUT -t filter'
This will show the chain with packet/byte counters that refresh every second, and with a helpful highlight: